http://www.comptechdoc.org/os/windows/win2k/index.html
People can go through with the left side list from 1 to 75
http://www.comptechdoc.org/os/windows/win2k/index.html
People can go through with the left side list from 1 to 75
1. Why not me?
2. Am I nice?
3. Am I doing what I really want to do?
4. What am I grateful for?
5. What’s missing in my life?
6. Am I honest?
7. Do I listen to others?
8. Do I work hard?
9. Do I help others?
10. What do I need to change about myself?
11. Have I hurt others?
12. Do I complain?
13. What’s next for me?
14. Do I have fun?
15. Have I seized opportunities?
16. Do I care about others?
17. Do I spend enough time with my family?
18. Am I open-minded?
19. Have I seen enough of the world?
20. Do I judge others?
21. Do I take risks?
22. What is my purpose?
23. What is my biggest fear?
24. How can I conquer that fear?
25. Do I thank people enough?
26. Am I successful?
27. What am I ashamed of?
28. Do I annoy others?
29. What are my dreams?
30. Am I positive?
31. Am I negative?
32. Is there an afterlife?
33. Does everything happen for a reason?
34. What can I do to change the world?
35. What is the most foolish thing I’ve ever done?
36. Am I cheap?
37. Am I greedy?
38. Who do I love?
39. Who do I want to meet?
40. Where do I want to go?
41. What am I most proud of?
42. Do I care what others think about me?
43. What are my talents?
44. Do I utilize those talents?
45. What makes me happy?
46. What makes me sad?
47. What makes me angry?
48. Am I satisfied with my appearance?
49. Am I healthy?
50. What was the toughest time in my life?
51. What was the easiest time in my life?
52. Am I selfish?
53. What was the craziest thing I did?
54. What is the craziest thing I want to do?
55. Do I procrastinate?
56. What is my greatest regret?
57. What has had the greatest impact on my life?
58. Who has had the greatest impact on my life?
59. Do I stand up for myself?
60. Have I settled for mediocrity?
61. Do I hold grudges?
62. Do I read enough?
63. Do I listen to my heart?
64. Do I donate enough to the less fortunate?
65. Do I pray only when I want something?
66. Do I constantly dwell on the past?
67. Do I let other people’s negativity affect me?
68. Do I forgive myself?
69. When I help someone do I think “What’s in it for me”?
70. Am I aware that someone always has it worse than me?
71. Do I smile more than I frown?
72. Do I surround myself with good people?
73. Do I take time out for myself?
74. Do I ask enough questions?
75. What other questions do I have?
Discovery Methods
Six methods of discovery are available in Configuration Manager 2007:
As Configuration Manager 2007 discovers resources, it creates records in the Configuration Manager database. This record is called a data discovery record (DDR) and the file generated has a .DDR extension. The specific information contained in each record varies depending on the resource "discovered," but it can include data such as the NetBIOS name of a computer, IP address and IP subnet of a computer or device, operating system, MAC address, and so on.
Depending on the discovery method used, resource DDRs are periodically regenerated to keep the discovery data up to date in the database and to verify that the resource is still a valid resource within the Configuration Manager 2007 site.
Now these methods what will discover?.. below are the discover use of each
Active Directory System Group Discovery
Organizational unit Global groups Universal groups Nested groups Nonsecurity groups
Active Directory System Discovery
Active Directory User Discovery
Network Discovery
Heartbeat Discovery :- Heartbeat Discovery is active only on computers that have already been installed as Configuration Manager clients.
It is important to ensure that any schedule you create causes the DDRs to be updated frequently enough so that the original DDR isn't viewed by Configuration Manager as obsolete or deleted from the database.Heartbeat Discovery updates existing DDRs rather than creating new ones. By default, it generates an updated DDR for each client every seven days, although this timing is configurable.
Heartbeat Discovery runs on installed Configuration Manager clients according to the schedule you specify. With this method enabled, the Client Component Installation Manager (CCIM) on the client causes the Cliex32.dll to generate a DDR, which is then written to the management point. This file is the same size as a normal DDR (approximately 1 KB per client), and so it will generate approximately the same network traffic.
Active Directory Security Group Discovery
he Configuration Manager 2007 Active Directory Security Group Discovery method searches for security groups by polling the closest Active Directory domain controller. The Active Directory domain can be in mixed mode or native mode.
Discovery Troubleshooting Flowcharts http://technet.microsoft.com/en-us/library/bb735871.aspx
Log files related to discovery
Adsysdis.log Active Directory System Discovery log file showing when the discovery method runs, and its results. Look for the number of DDRs created and any "bogus" entries.
Adsysgrp.log Active Directory System Group Discovery log file showing when the discovery method runs, and its results. Look for the number of DDRs created.
Adusrdis.log Active Directory User Discovery log file showing when the discovery method runs, and its results. Look for the number of DDRs created.
DISCOVERY HAS A DEPENDENCE OF CLEINT PUSH, IF DISCOVERY IS NOT ENABLED OR NOT DISCOVERED ANY SYSTEMS THEN CLIENT PUSH WILL NOT PUSH ON ANY SYSTEM’S
Scripts:- http://technet.microsoft.com/en-us/library/cc180843.aspx
If you deleted any system from SCCM / SMS console you can initiate the client discovery data cycle then client can be reappear in the console
Third party Discovery Tools :- enhanced discovery tool
The major discovery drop backs in SCCM is it will not do a delta discovery it will do from scratch.. that means it will not discover specific to the changes that has changed from last cycle.. to accomplish this you need to depend on Enhanced discovery tool http://www.systemcentertools.com/esd.html
now with SCCM R3 you can do delta discovery
 If SMS/SCCM Client is installed we will get SMS Agent host (ccmexec.exe ) service will be installed all the related information log file is ccmexec.log file
If SMS/SCCM Client is installed we will get SMS Agent host (ccmexec.exe ) service will be installed all the related information log file is ccmexec.log file
if client installed it will come in Control Panel
if the client OS version is 32 bit then you can find the applets in the control panel directly, if it is 64 bit OS then you will get in 32-bit Control Panel items (The reason is sccm is a 32 bit application) also client will be installed in windows\ccmsetup for client installation
and for client logs in 64 located in
64 bit client log files location screenshot is below
Above is a example screenshot
There are 3 areas of consideration when troubleshooting access to the SMS provider and the site server.
1. Do you have the necessary privileges to the SMS provider on your site server?
2. Do you have the necessary security rights to the database?
3. Do you have the necessary privileges as far as WBEM is concerned?
4. Is WBEM working?
http://www.myitforum.com/articles/6/view.asp?id=250
http://support.microsoft.com/kb/317872
Verify that this computer has network connectivity to the SMS Provider
http://technet.microsoft.com/en-us/library/bb932213.aspx
Check the adminui.log and smsprov.log and smsdbmon.log
1. Add the Configuration Manager Secondary Site Server Computer account to the Group “SCCM-GROUP”. As mentioned in my previous article this group must be added on to the System Management Container Security tab with Full permissions in active directory users and computers snap in as shown below.
2. Add the computer account of Configuration Manager Secondary site server to the Local Group “SMS_SiteToSiteConnection_INC” which is present on the primary Site server.
Procedure:
Logon to primary Site Server- Open Computer management drill down to Local Users and Groups, Select groups and in that we will find a Local Group named as “SMS_SiteToSiteConnection_INC” as shown below. Go to the properties page and add secondary site server computer account.
3. Create a Sender Address with the Secondary Site Code and Primary Site Information.
Procedure:
Open SCCM2007 Primary Site Server management Console, drill down to Site Management-Site Code- Site Settings- Addresses.
Right Click on Addresses and create a new Standard Sender Address
On the new Standard Sender Address Wizard, enter the Destination Site Code that is the new site code which we will give at the time of Secondary Site server installation. In our case we will give INS.
Give the Site Server name that is the Secondary Site Server Name.
If you leave the Site address account empty, the sender will use Primary Site Computer account to establish communication between both the sites (Primary and Secondary). If you leave the default, Primary site computer account must have full permissions on the secondary site server.
We can also set a windows user account that is having full admin privileges on both the site servers.
In our case we will leave as it is to use the Primary site Computer account.
In our case we selected open from Sunday to Saturday and click next
Leave the defaults and click Finish, you can also modify these settings based on your organization needs.
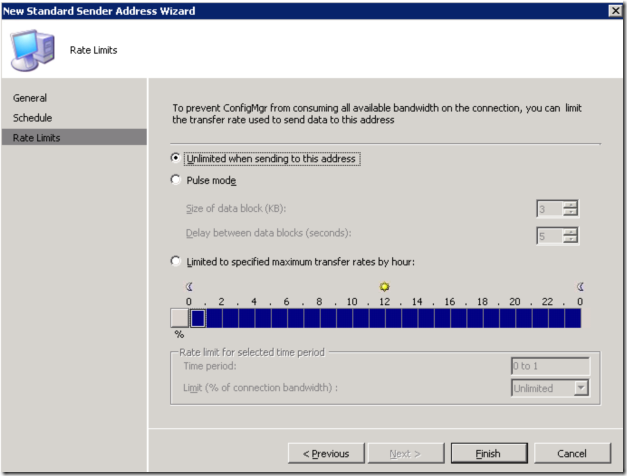
Once done you will see the newly created connector as shown below.
4. Check the remote installation permissions of the account with which we are installing SCCM2007.
As discussed previously, we are using the Site server system account to establish communication between 2 sites, make sure we add the SCCM-Group into the Local Administrators group on the Configuration Manager Secondary Site Server.
To verify these
Log onto the Secondary site server and add the SCCM-GROUP account in the Local Administrators group of SCCM2007 Secondary site server.
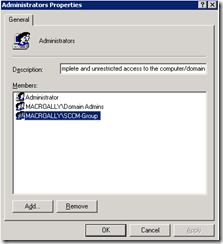
5. The SCCM2007 Primary site server Computer account must have full admin privileges on the Secondary Site Server computer account.
6. The Service account with which we are installing secondary site server must have local admin privileges on the Secondary Site Computer account.
7. Install IIS 6.0 (IIS is used for Management Point and Fallback Status Point)
Installing secondary site is two methods one from SCCM Console and second one from direct media from secondary site. we will run with the second option.
On the installation Prerequisite Check windows select Secondary site and click ok
click OK
Click ok, and
Initiate the Configuration Manager 2007 installation
Click next on the available setup options page
Accept the License agreement and click next
On the site type windows select Secondary site and click next
Provide the installation directory for binary files and click next
On the Site Settings Windows Insert the site code which we entered at the time of Sender creation and provide the site name
In our case site code is INS and Site Name is MacroALLY Secondary Site Server
On the Parent Site Settings window, enter the Primary site code, which are INC and the Parent Site Server Name. Click next to proceed
On the Update Prerequisite Components page leave the defaults and click next
On the Updated Prerequisites path, enter the path to the folder were SCCM will download the updates and put it. Click next
On the settings summary page review the settings, if any changes go back to modify or proceed further with installation by clicking next
Setup will evaluate your system and cross checks all the prerequisites once more, if the status is green proceed further by clicking Begin install.
Setup starts installing the Configuration Manager Secondary site server
Click Finish and restart the server
open the console now after restart
And the Sender will be updated with the necessary information as shown below
Vise Versa in the Secondary site settings-Address, you will also see a sender address created for Primary server as shown below
Configuration Manager Secondary Site is installed Secondary Site Information is updated in the System management Container in AD which is shown below
How confirm that Secondary site is working /Primary to secondary communication is fine:
Verify the Log Files to find out weather Secondary site is communicating with primary server properly.
Log files to monitor
ConfigMgrSetup.Log : Located on the root of system drive (Secondary site server )
Sender.log: Located on the Secondary site server installation directory (c:\Program Files\Microsoft Configuration Manager\Logs\Sender. Log) used to track weather the site is sending site information to the primary parent site.
After ensuring there are no communication problems from the above 2 logs, go ahead to check the despoiler.log on the primary site server to ensure it has received the secondary site information and is processing the secondary site information.
Despoole.log: located on the Primary site server (c:\Program Files\Microsoft Configuration Manager\ Logs\Despool.log)
Hman.log: Logs actions related to the hierarchy structure of the sites, located on the primary server (c:\Program Files\Microsoft Configuration Manager\ Logs\HMan.log).
Sitecomp.log: Logs information related to secondary site information publishing to Active Directory along with the primary site information, Located on the primary Site Server (c:\Program Files\Microsoft Configuration Manager\ Logs\SiteComp.log)
With this you are done with Secondary site Server Installation.
Site Status components are at least 51 or more than that are available. And here below of some mentioned may need to come as read / warning in your day to day operations
SMS_LAN_SENDER
SMS_EXECUTIVE
SMS_HIERARCHY_MANAGER
SMS_DISTRIBUTION_MANAGER
SMS_DESPOOLER
SMS_DISCOVERY_DATA_MANAGER
SMS_INBOX_MANAGER
SMS_MP_CONTROL_MANAGER
SMS_MP_FILE_DISPATCH_MANAGER
SMS_INVENTORY_PROCESSOR
SMS_INBOX_MONITOR
SMS_INVENTORY_DATA_LOADER
SMS_DATABASE_NOTIFICATION_MONITOR
SMS_AD_SYSTEM_GROUP_DISCOVERY_AGENT
SMS_AI_KB_MANAGER
SMS_AMT_PROXY_COMPONENT
SMS_SITE_SQL_BACKUP_AUPERPSPSS01
SMS_AD_SECURITY_GROUP_DISCOVERY_AGENT
SMS_AD_SYSTEM_DISCOVERY_AGENT
SMS_COMPONENT_MONITOR
SMS_COMPONENT_STATUS_SUMMARIZER
SMS_CLIENT_CONFIG_MANAGER
SMS_COLLECTION_EVALUATOR
SMS_WSUS_CONFIGURATION_MANAGER
SMS_WSUS_CONTROL_MANAGER
SMS_SOFTWARE_METERING_PROCESSOR
SMS_STATE_SYSTEM
SMS_STATUS_MANAGER
SMS_MP_FILE_DISPATCH_MANAGER
SMS_OUTBOX_MONITOR
SMS_PXE_SERVICE_POINT
SMS_WSUS_SYNC_MANAGER
SMS_COMPONENT_MONITOR
SMS_EXECUTIVE
SMS_SOFTWARE_INVENTORY_PROCESSOR
SMS_OUTBOX_MONITOR
SMS_POLICY_PROVIDER
SMS_REPLICATION_MANAGER
SMS_OBJECT_REPLICATION_MANAGER
SMS_OFFER_MANAGER
SMS_SITE_BACKUP
SMS_SITE_COMPONENT_MANAGER
And out of the regular ones in my case I am seeing these many times in the hierarchy
SMS_LAN_SENDER==================> in the error mentioned site systems are offline or network connectivity problem
SMS_DISTRIBUTION_MANAGER========> Targeted packages are not reached the DP or very frequently updated by some one
SMS_MP_CONTROL_MANAGER==========>
Mpcert http://sccmserverName/sms_mp/.sms_aut?mpcert
MPlist http://sccmserverName/sms_mp/.sms_aut?mplist
For MP function mpcontrol.log file.. You may get 401,403 or 500 errors mostly with IIS & SQL issues. If you see error 200 that means MP working Fine.
Log files location for a server with the sitecode of DC1
SMS_COLLECTION_EVALUATOR========> at this stage we can ignore this error
SMS_WSUS_SYNC_MANAGER===========> Solution: - open the wsyncmgr.log file check for errors and do a more sync if required from below given screenshot
Sample Error:- SMS WSUS Configuration Manager failed to configure proxy settings on WSUS Server "USDC1PSPSS02".
Possible cause: WSUS Server version 3.0 SP1 and above is not installed or cannot be contacted.
Solution: Verify that the WSUS Server version 3.0 SP1 or greater is installed. Verify that the IIS ports configured in SMS are same as those configured on the WSUS IIS website.You can receive failure because proxy is set but proxy name is not specified or proxy server port is invalid.
SMS_OUTBOX_MONITOR============> You need to connect to the Configmgr Service Manager and stop the inbox_monitor component and start it same applies to below one.
SMS_Inboxe_MONITOR=============>
SMS_PXE_SERVICE_POINT===========> Check the WDS Service in Services.msc console if the service is stopped raise a P-4 incident to start the service. MAKE SURE IF THE SERVICE IS IN STARTED STATE AND YOU ARE TRYING TO STOP IT MAY CHANGE THE STATUS TO STOPPING STATUS AND IT NEVER CHANGES IT STATUS TO RUNIING OR STOPPED STATE, AND It will not allow you to even kill the pid The solution is reboot the system (This also happens to SMS executive service also)
What is Active Directory? (This article taken it from http://learnthat.com and all rights and credits goes to http://learnthat.com)
Active Directory (AD) is a technology created by Microsoft to provide network services including LDAP directory services, Kerberos based authentication, DNS naming, secure access to resources, and more. Active Directory uses a single Jet database![]() which a variety of services and applications can use to access and store a variety of information. Active Directory is used by system administrators to store information about users, assign security policies, and deploy software. AD is used in many different types and size of environments from the very small (a dozen users) to hundreds of thousands of users in a global environment.
which a variety of services and applications can use to access and store a variety of information. Active Directory is used by system administrators to store information about users, assign security policies, and deploy software. AD is used in many different types and size of environments from the very small (a dozen users) to hundreds of thousands of users in a global environment.
In this tutorial, you will learn the basic structure of Active Directory, gain an understanding of how Active Directory works, learn how to install Active Directory, and learn the components of AD.
This tutorial is divided into these sections:
What is Active Directory: An overview of Active Directory and its use in technology environments.
Active Directory Structure: Learn the basics of AD, its components (such as domains![]() , domain controllers, trust relationships, forests, organizational units, etc), hierarchies within AD, and DNS.
, domain controllers, trust relationships, forests, organizational units, etc), hierarchies within AD, and DNS.
How to Install Active Directory: Active Directory installation is not complex in its process, but can be difficult in the future if you do not plan the installation correctly. Learn the tricks and tips you need to know to properly plan an AD installation and why administrators install AD the way they do.
This free Active Directory tutorial is not a comprehensive one on the topic, but an introduction to Active Directory and its structure and use.
History of Active Directory
Active Directory was introduced to the world in the mid-1990s by Microsoft as a replacement for Windows NT-style user authentication. Windows NT included a flat and non-extensible domain model which did not scale well for large corporations. Active Directory, on the other hand, was created as a true directory service versus a flat user-management service that NT had. Though it was introduced in the 1990s, it did not become a part of the Operating System until Windows 2000 Server was released in 2000. Since then, Windows Server 2003 and Server 2008 have been introduced and Active Directory has gone under some expansion.
This tutorial is based on Windows Server 2003 as it is currently the most widely installed version of the Windows network Operating System (NOS), though in the future we will release versions for Windows Server 2008 and future Windows releases as it becomes necessary. Though this tutorial is not focused on Windows Server 2008, much of the basic knowledge and instruction relates to either OS.
LDAP
Active Directory is based loosely on LDAP – Lightweight Directory Access Protocol – an application protocol for querying and modifying directory services developed at the University of Michigan in the early 1990s. An LDAP directory tree is a hierarchical structure of organizations, domains, trees, groups, and individual units.
Example of an LDAP Tree
Active Directory is a Directory
Sometimes, it’s easy to get lost in all of the technology and functions that are provided with AD and forget that Active Directory is a directory. It is a directory in both the common use of the term like a white pages (you can add in a person’s first name, last name, phone number, address, email address, etc) and a directory of information for use by applications and services (such as Microsoft Exchange for email). AD is functionally a place to store information about people, things (computers, printers, etc), applications, domains, services, security access permissions, and more. Applications and services then use the directory to perform a function.
For example, Microsoft Windows uses Active Directory information to allow a user to login to their computer and provide access to the security rights assigned in Active Directory. Windows is accessing the directory and then providing rights based on what it finds. If a user account is disabled in Active Directory, the directory itself is just setting a flag which Windows uses to disallow a user from logging in.
We mentioned in the introduction that administrators use Active Directory to deploy software – this is an incomplete description. Administrators can set policies and information that a certain software application should be deployed to a certain user – AD itself does not deploy the software, but a Windows service reads the information from Active Directory and then installs the software.
Once you grasp the concept that Active Directory is a directory, you’re halfway to understanding why it is built the way it is!
Unlike Windows NT![]() , Active Directory is designed for you to create a functional and usable hierarchy for your environment. Not only does this make the environment look cleaner, but it also allows central system administrators to delegate specific authority over areas to other administrators, team members, and groups. AD has a very flexible structure, allowing you to build a hierarchy in whatever way you wish – one big unit, broken down by geographic location, by department, by astronomical sign, or however you desire.
, Active Directory is designed for you to create a functional and usable hierarchy for your environment. Not only does this make the environment look cleaner, but it also allows central system administrators to delegate specific authority over areas to other administrators, team members, and groups. AD has a very flexible structure, allowing you to build a hierarchy in whatever way you wish – one big unit, broken down by geographic location, by department, by astronomical sign, or however you desire.
Achieving this flexibility in hierarchical design is a defined structure. The structure of Active Directory starts with forests and domains![]() and goes down to organizational units and individual objects (such as a user or computer account). The flexibility in hierarchical design is a benefit to network architects, but if you do not design the structure correctly in the beginning, it can be a nightmare down the road. We recommend spending a lot of time thinking about the best hierarchical structure for your Active Directory environment before diving in and building it.
and goes down to organizational units and individual objects (such as a user or computer account). The flexibility in hierarchical design is a benefit to network architects, but if you do not design the structure correctly in the beginning, it can be a nightmare down the road. We recommend spending a lot of time thinking about the best hierarchical structure for your Active Directory environment before diving in and building it.
In this section, we are going to look at the basic building blocks of Active Directory – all those things which make it such a flexible directory service.
Basic Active Directory Components
At its core, Active Directory needs structure to work properly. It provides the basic building blocks for people to build their own directory. These basic building blocks of Active Directory include domains![]() , domain controllers, trusts, forests, organizational units, groups, sites, replication, and the global catalog.
, domain controllers, trusts, forests, organizational units, groups, sites, replication, and the global catalog.
Understanding Forests
At the top of the Active Directory structure is a forest. A forest holds all of the objects, organizational units, domains, and attributes in its hierarchy. Under a forest are one or more trees which hold domains, OUs, objects, and attributes.
As illustrated in this image, there are two trees in the forest. You might use a structure like this for
organizations with more than one operating company.
You could also design a structure with multiple forests, but these are for very specific reasons and not common.
Domains
At the heart of the Active Directory structure is the domain. The domain is typically of the Internet naming variety (e.g. Learnthat.com), but you are not forced to stick with this structure – you could technically name your domain whatever you wish.
Microsoft recommends using as few domains and possible in building your Active Directory structure and to rely on Organizational Units for structure. Domains can contain multiple nested OUs, allowing you to build a pretty robust and specific structure.
Domain Controllers
In Windows NT, domains used a Primary Domain Controller (PDC) and Backup Domain Controller (BDC) model. This had one server, the PDC, which was “in charge” while the other DCs where subservient. If the PDC failed, you had to promote a BDC to become the PDC and be the server in charge.
In Active Directory, you have multiple Domain Controllers which are equal peers. Each DC in the Active Directory domain contains a copy of the AD database and synchronizes changes with all other DCs by multi-master replication. Replication occurs frequently and on a pull basis instead of a push one. A server requests updates from a fellow domain controller. If information on one DC changes (e.g. a user changes their password), it sends signal to the other domain controllers to begin a pull replication of the data to ensure they are all up to date.
Servers not serving as DCs, but in the Active Directory domain, are called ‘member servers.’
Active Directory requires at least one Domain Controller, but you can install as many as you want (and it’s recommended you install at least two domain controllers in case one fails).
Trust Relationships
Trust Relationships are important in an Active Directory environment so forests and domains can communicate with one another and pass credentials. Within a single forest, trusts are created when a domain is created. By default, domains have an implicit two-way transitive trust created. This means each domain trusts each other for security access and credentials. A user in domain A can access resources permitted to him in domain B while a user in domain B can access resources permitted to her in domain A.
AD allows several different types of trusts to be created, but understanding the two-way transitive trust is the most important to understanding AD.
Organizational Units
An Organizational Unit (OU) is a container which gives a domain hierarchy and structure. It is used for ease of administration and to create an AD structure in the company’s geographic or organizational terms.
Organizational Units
An OU can contain OUs, allowing for the creating of a multi-level structure, as shown in the image above. There are three primary reasons for creating OUs:
Organizational Structure: First, creating OUs allows a company to build a structure in Active Directory which matches their firm’s geographic or organizational structure. This permits ease of administration and a clean structure.
Security Rights: The second reason to create an OU structure is to assign security rights to certain OUs. This, for example, would allow you to apply Active Directory Policies to one OU which are different than another. You could setup policies which install an accounting software application on computers in the Accounting OU.
Delegated Administration: The third reason to create OUs is to delegate administrative responsibility. AD Architects can design the structure to allow local administrators certain administrative responsibility for their OU and no other. This allows for a delegated administration not available in Windows NT networks.
Groups
Groups serve two functions in Active Directory: security and distribution.
A security group contains accounts which can be used for security access. For example, a security group could be assigned rights to a particular directory on a file server.
A distribution group is used for sending information to users. It cannot be used for security access.
There are three group scopes:
Global: Global scope security groups contains users only from the domain in which is created. Global security groups can be members of both Universal and Domain Local groups.
Universal: Universal scope security groups can contain users, global groups, and universal groups from any domain. These groups are typically used in a multi-domain environment if access is required across domains.
Domain Local: Domain Local scope groups are often created in domains to assign security access to a particular local domain resource. Domain Local scope groups can contain user accounts, universal groups, and global groups from any domain. Domain Local scope groups can contain domain local groups in the same domain.
Sites
An Active Directory site object represents a collection of IP subnets, usually constituting a physical Local Area Network (LAN). Multiple sites are connected for replication by site links. Typically, sites are used for:
Physical Location Determination: Enables clients to find local resources such as printers, shares, or domain controllers.
Replication: You can optimize replication between domain controllers by creating links.
By default, Active Directory uses automatic site coverage, though you can purposefully setup sites and resources.
Replication
Since most Active Directory networks contain multiple domain controllers and users could theoretically attach to any DC for authentication or information, each of the servers needs to be kept up to date. Domain Controllers stay up to date by replicating the database between each other. It performs this using a pull method – a server requests new information from a different DC frequently. After a change, the DC initiates a replication after waiting 15 seconds (in Windows 2003) or 5 minutes (in Windows 2000). Windows Server 2003![]() uses technology to only replicate changed information and compressions replication over WAN links.
uses technology to only replicate changed information and compressions replication over WAN links.
Windows Server sets up a replication topology to determine where a server updates from. In a large network, this keeps replication time down as servers replicate in a form of a ring network.
Active Directory uses multi-master replication. Multimaster replication does not rely on a single primary domain controller, but instead treats each DC as an authority. When a change is made on any DC, it is replicated to all other DCs. Although each DC is replicated alike, all of the DCs aren’t equal. There are several flexible single-master operation roles which are assigned to one domain controller at a time.
AD uses Remote Procedure Calls (RPC) for replication and can use SMTP for changes to schema or configuration.
FSMO Roles
All domain controll
ers are not equal. We know, it’s hard to hear. You’ve spent this whole time reading this tutorial thinking that all DCs are created equal and now we have to burst your bubble. Some DCs have more responsibility than others. It’s just part of life!
There are five roles which are called operations masters, or flexible single-master operations (FSMOs). Two are forestwide roles and three are domainwide roles. The forestwide roles are:
Schema master: Controls update to the Active Directory schema.
Domain naming master: Controls the addition and removal of domains from the forest.
The three domainwide roles are:
RID master: Allocates pools of unique identifier to domain controllers for use when creating objects. (RID is relative identifier).
Infrastructure master: Synchronizes cross-domain group membership changes. The infrastructure master cannot run on a global catalog server, unless all of the DCs are global catalog servers.
PDC Emulator: Provides backward compatibility for NT 4 clients for PDC operations – such as a password change. The PDC also serves as the master time server.
Global Catalog
As a network gets larger, it can contain multiple domains and many domain controllers. Each domain only contains records from its own domain in its AD database to keep the database small and replication manageable. The Active Directory domain relies on a global catalog database which contains a global listing of all objects in the forest. The Global Catalog is held on DCs configured as global catalog servers.
The global catalog contains a subset of information – such as a user’s first name and last name – and the distinguished name of the object so your client can contact the proper domain controller if you need more information. The distinguished name is the full address of an object in the directory. For example, a printer in the OU Accounting in the Learnthat.com domain might have a distinguished name of:
CN=AcctLaser1,OU=Accounting,DC=Learnthat,DC=com
The GC database is only a subset of the entire database called the Partial Attribute Set (PAS), containing 151 of the 1,070 properties available in Windows Server 2003. You can define additional properties for replication to the GC by modifying schema.
Active Directory Hierarchies
Now that you understand the building blocks of Active Directory, you can start to understand how to build a hierarchy in Active Directory. One of the foundations of design for AD has been a flexibility to allow companies to build a structure which fits into their organization. This flexibility allows organizations of all sizes to use Active Directory to meet their needs.
Domains and OUs
The most basic design of an Active Directory is a single forest, single domain, no Organizational Unit design.
Basic AD Installation
For a small organization, this might be adequate, but almost every organization can benefit from some structure.
Creating multiple domains![]() is not always the best design solution, so Microsoft created organizational units in Active Directory which can be nested to provide hierarchical control of your AD environment. It is a great idea to think about and map out your OU design before committing it into Active Directory.
is not always the best design solution, so Microsoft created organizational units in Active Directory which can be nested to provide hierarchical control of your AD environment. It is a great idea to think about and map out your OU design before committing it into Active Directory.
Typically, companies design their OU trees based on either geographic separation (e.g. Americas, EMEA, PacificRim) or based on organizational design (e.g. Accounting, Marketing, Technology, Sales). There is no incorrect way to design your AD environment, however, consistency should be key. You shouldn’t mix the two design methods and have a top level Americas OU and a top level Sales OU. Doing so makes administration difficult as you won’t know where a particular salesperson’s account is.
Also, remember that OUs allow enterprise administrators to delegate administration responsibility to local teams. Building an effective OU design will allow you to properly delegate authority.
The other reason OUs are used is to apply policies. Policies are rules for security, access, and functionality which can apply to several different containers in Active Directory. Frequently, policies are applied by OU – so though you might separated geographically (and therefore want to set up your structure based solely on geography), it might make more sense to setup your AD by organizational divisions. Why? Because if all of your marketing employees need the same software and settings, you will setup policies based on the department instead of the physical location of the employees.
Domain Trees
Once an organization becomes large and you cannot have the entire AD database![]() replicated everywhere, it might make sense to move to a domain tree. A domain tree allows an organization to become more decentralized as it is more independent than using an OU tree.
replicated everywhere, it might make sense to move to a domain tree. A domain tree allows an organization to become more decentralized as it is more independent than using an OU tree.
Domain-wide policies can be changed per domain in a domain tree which is not possible with only an OU structure. Policies such as minimum and maximum password age, minimum password length, and account lockout are domain-wide policies and cannot be changed on a per-OU basis. By creating multiple domains, administrators can set these policies for each domain.
Domain Tree
In the illustration above, learnthat.com has a domain tree in the Active Directory domain.
Forest of Domain Trees
In more complex environments, a company may use multiple domain trees in a single forest. This might be a large operating company with multiple subsidiaries – each requiring their own domain, for example, ThatNetwork.com is the parent company and subsidiaries might include Learnthat.com, Romancetips.com, Exampractice.com. This structure makes sense if you have different administrative staff for each domain, along with different policies and different security requirements.
You can still setup trusts between the domains to allow users to authenticate for resources in either domain.
Multiple Forests
The last possibility is using multiple forests. This is the less frequent design choice, but can be used with you want an absolute separation for one reason or another. This structure is most often found when companies merge or in the case of acquisitions. In Windows 2003, you can setup forest trusts between forests to allow some access.
DNS
Active Directory is integrated with Domain Naming System (DNS) and requires it to be present to function. DNS is the naming system used for the Internet and on many Intranets. You can use DNS which is built into Windows 2000 and newer, or use a third party DNS infrastructure such as BIND if you have it in the environment. It is recommended you use Window’s DNS service as it is integrated into Windows and provides the easiest functionality.
AD uses DNS to name domains![]() , computers, servers, and locate services.
, computers, servers, and locate services.
A DNS server![]() maps an object’s name to its IP address. For example, on the Internet, it is used to map a domain name (such as www.learnthat.com) to an IP address (such as 64.34.165.234). In an Active Directory network, it is used n
maps an object’s name to its IP address. For example, on the Internet, it is used to map a domain name (such as www.learnthat.com) to an IP address (such as 64.34.165.234). In an Active Directory network, it is used n
ot only to find domain names, but also objects and their IP address. It also uses service location records (SRV) to locate services.
Active Directory Installation
Some larger organizations take months (and in some cases, over a year) to plan a proper Active Directory design and get input from a global organization of technology leaders. It is extremely important to give a lot of thought to your AD design to ensure it meets your organization’s needs.
Choosing Your AD Layout
As we mentioned earlier, there are many ways you can structure your Active Directory. From a top level down perspective, most companies either start with a geographic separation or a organizational structure separation, for example Americas, EMEA, PacificRIM for geographic or Accounting, Marketing, Technology, Sales for organizational structure. It does not matter which you select: either will provide a fine starting point for your domain structure, but you need to ensure you pick one direction and be consistent with your choices.
Many organizations start with geography at the top level, then break down into business units or departments underneath that top level. It is important to write naming conventions and standards down so a team in Europe does not call an OU “SalesMarketing” while a team in North America calls an OU “Sales.” Consistency provides for an efficient and manageable Active Directory layout.
There are many different combinations you could choose when designing your AD structure.
Installation Requirements
In this section, we will look at the installation requirements of Active Directory. Installing AD isn’t a complex process, but the design and configuration can be.
Here are the requirements for installing Active Directory on Windows Server 2003:
· An NTFS partition with enough free space
· An Administrator’s username and password
· NIC with Network Connection
· Properly configured TCP/IP (IP address, subnet mask and – optional – default gateway)
· An operational DNS server (which can be installed on the DC itself)
· A Domain name that you want to use
· Windows Server 2003 CD media or the i386 Folder
Functional Levels
In Windows 2000, you chose from two levels: mixed mode or native mode. When Windows 2000 Server was introduced, NT 4 was still a popular server option. To ensure backward compatibility with these servers and clients, Windows 2000 defaulted to mixed mode where you could add Windows NT 4 servers to the Windows 2000 Active Directory domain.
Windows Server 2003 introduced functional levels – a set level of backward compatibility for previous operating systems. If you are in an environment with NT 4 servers and Windows 2000 servers which are still accessed, you can set a functional level to ensure backwards compatibility.
Windows 2003 expands from those two modes to one of many domain functional levels including Windows 2000 Mixed, Windows 2000 Native, Windows Server 2003 Interim, and Windows Server 2003. Also, in Windows Server 2003, you have three forest functional levels available: Windows 2000, Windows Server 2003 Interim, or Windows server 2003. Each functional level brings new features available and lose compatibility with some set of servers or clients.
By default, Windows Server 2003 starts at Windows 2000 Mixed functional level. Not all of the features of 2003 are available in this mode, so if you are designing a new Windows 2003 AD environment, you will want to take advantage of the new features added in Windows Server 2003.
In Windows 2000, we referred to this change as “changing the mode,” but in Windows 2003, we now raise the functional level with either Active Directory Users and Computers or Domains and Trusts.
This change cannot be reversed – once you make a decision to raise the functional level, you cannot go back to a lower functional level.
Active Directory
Please note: these installation instructions are for a brand new domain – not for adding a server as a member server or domain controller in an existing domain. Following these instructions in a production network is not recommended.
We are going to review the AD installation process from a clean install of Windows Server 2003. You may have already set some of these settings, so look through the steps and perform any tasks you have failed to do.
Set Network Settings
1. This server will be both a domain controller and a DNS server, so we are going to set a static IP address.
2. Click Start, Control Panel, Network Connections and select your network connection.
3. Click Properties.
4. Click Internet Protocol (TCP/IP) and click Properties.
5. Enter in your static IP address information and preferred DNS servers. Notice one of the DNS servers I listed is the server itself – this will be a DNS server in a minute.
6. Click OK.
7. Click Close.
8. Click Close.
9. Click Start. Right-click on My Computer and select Properties.
10. Click on the Computer Name tab.
11. Click on the More button.
12. Enter in the domain name you are going to be using for your AD domain in the Primary DNS suffix of this computer text field.
13. Click OK.
14. Click OK. Acknowledge that you have to reboot and click OK.
15. Click Yes to the prompt asking you if you wan
t to reboot.
Install the DNS Service
16. On the Manage Your Server window, select Add or remove a role. (Don’t see this window at startup? Find it at Start > All Programs > Administrative Tools > Manage Server)
17. Click Next.
18. Click DNS Server and click Next.
19. Click Next.
20. Insert your Windows Server 2003 setup cd and click OK.
21. Navigate to where the i386 folder is and click OK.
22. Click Next to start the DNS wizard.
23. Click Next to create a forward lookup zone.
24. Click Next that this server retains a the zone.
25. Name your zone with your domain name. Click Next.
26. Accept the default filename and click Next.
27. Click Allow both nonsecure and secure dynamic updates. Click Next.
28. Select whether or not this DNS server should forward queries. If you use an ISP for DNS resolution for Internet sites, enter in your ISP’s DNS servers in the first option. If this DNS server will resolve all queries, select the second option. Click Next.
29. Click Finish.
30. Click Finish.
31. Congratulations! You have setup a DNS server!
Setting Up Active Directory
32. On the Manage Your Server window, click Add or remove a role.
33. Click Next.
34. Select Domain Controller (Active Directory) and click Next.
35. Click Next.
36. Click Next when the Active Directory wizard opens.
37. Click Next.
38. Click Next.
39. Click Next.
40. Enter in your domain name and click Next.
41. Enter in a NetBIOS name or accept the default and click Next.
42. Click Next to accept the default locations for the database![]() and log, or select a location for these files.
and log, or select a location for these files.
43. Enter a location for the Shared System Volume and click Next.
44. Click Next.
45. Click Next.
46. Enter in a password and click Next.
47. Click Next.
48. The wizard will configure Active Directory.
49. Click Finish to complete the wizard.
50. Click Restart Now.
Congratulations,
Creating Organizational Units
As we discussed earlier, Organizational Units provide a mechanism to design a hierarchical structure within your Active Directory environment. Once you have designed your AD structure, you are ready to create the OUs in the environment.
1. Click Start > Administrative Tools > Active Directory Users and Computers.
2. Double-click the domain name to open it up.
3. You will see a default structure with no Organizational Units. Right-click on the domain name and select New > Organizational Unit.
4. Enter the name of the OU you want to create and click OK.
5. You will now see the OU you just created. Continue the process and build out the top level OUs.
6. You now have a structure from which to build your organizational structure. For a small organization, we would create a Users and Computers organizational unit under each of the top level OUs.
7. Right-click on Accounting and select New > Organizational Unit and enter in Computers. Click OK. Repeat this process for the Users OU.
8.  
; Now repeat the process for each department and you will have a structure of OUs created
Post Active Directory Install
There are several steps you should do after the Active Directory installation to ensure installation went correctly and make sure AD operates properly in your environment.
Verify Installation
After you have installed Active Directory, there are several steps you can take to ensure setup functioned correctly.
First, you can ensure the AD tools are installed. Click on Start and click Administrative Tools. You should have these tools installed:
Next, open Active Directory Sites and Services. You should have a Default-First-Site-Name listed and when you open it up, you should find your domain controller listed as a server.
Finally, open up DNS management. Open up the DNS server name, the Forward Lookup Zones, the domain name, and _tcp. It should look like this with four SRV records:
Once you’ve performed these tasks, you’ve confirmed that your AD environment is installed.
Management Utilities
There are several management utilities you use to manage the Active Directory environment. As you saw after installation, you have these utilities (which are MMC snap-ins):
Active Directory Domains and Trusts: Manage domains and trusts between domains using this tool.
Active Directory Sites and Services: Setup and manage sites (physical networks).
Active Directory Users and Computers: Create and manage users, computers, other objects, OUs.
By accessing this Website, you indicate your acknowledgement acceptance of the following terms and conditions. These terms and conditions may change from time to time, and you agree to be bound by any such changes when posted on this Website, including its affiliates, as applicable reserves all of its rights at law and equity, The information and content displayed on this Website, including but not limited to text, graphics, logos, images, audio clips and software, is the property of Public or its licensors, as the case may be, and is protected by copyright laws. While I invite you to browse, no content or information on this Website may be downloaded, reproduced or modified in any manner without the prior written consent of me (PaddyMaddy) or as otherwise expressly provided herein.